Cybersecurity: Internet security 101: Six ways hackers can attack you and how to stay safe - The Economic Times

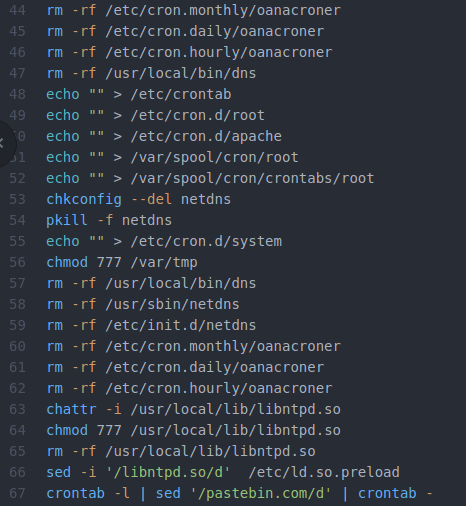
Attacking A Virtual Toaster: An Experiment Shows How Quickly The Internet Of Things Can Be Hacked : All Tech Considered : NPR
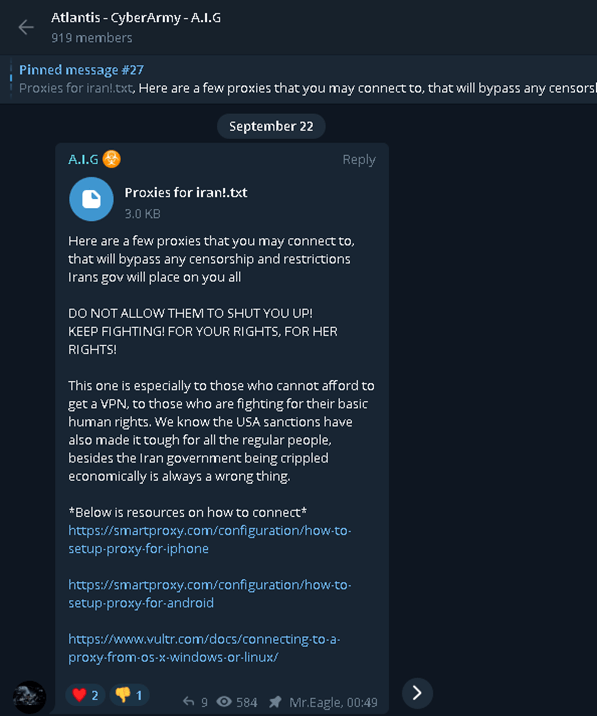
Hacker Groups take to Telegram, Signal and Darkweb to assist Protestors in Iran - Check Point Software

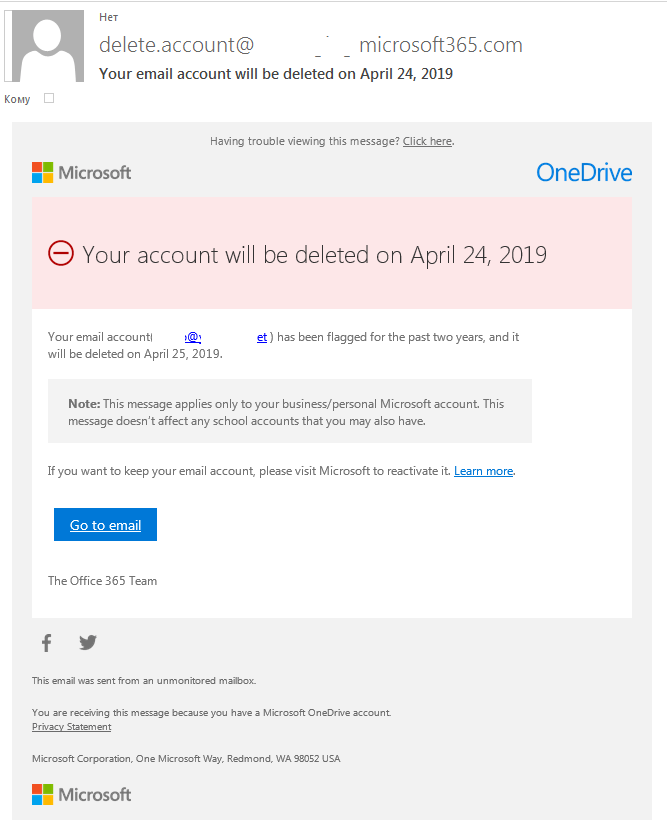
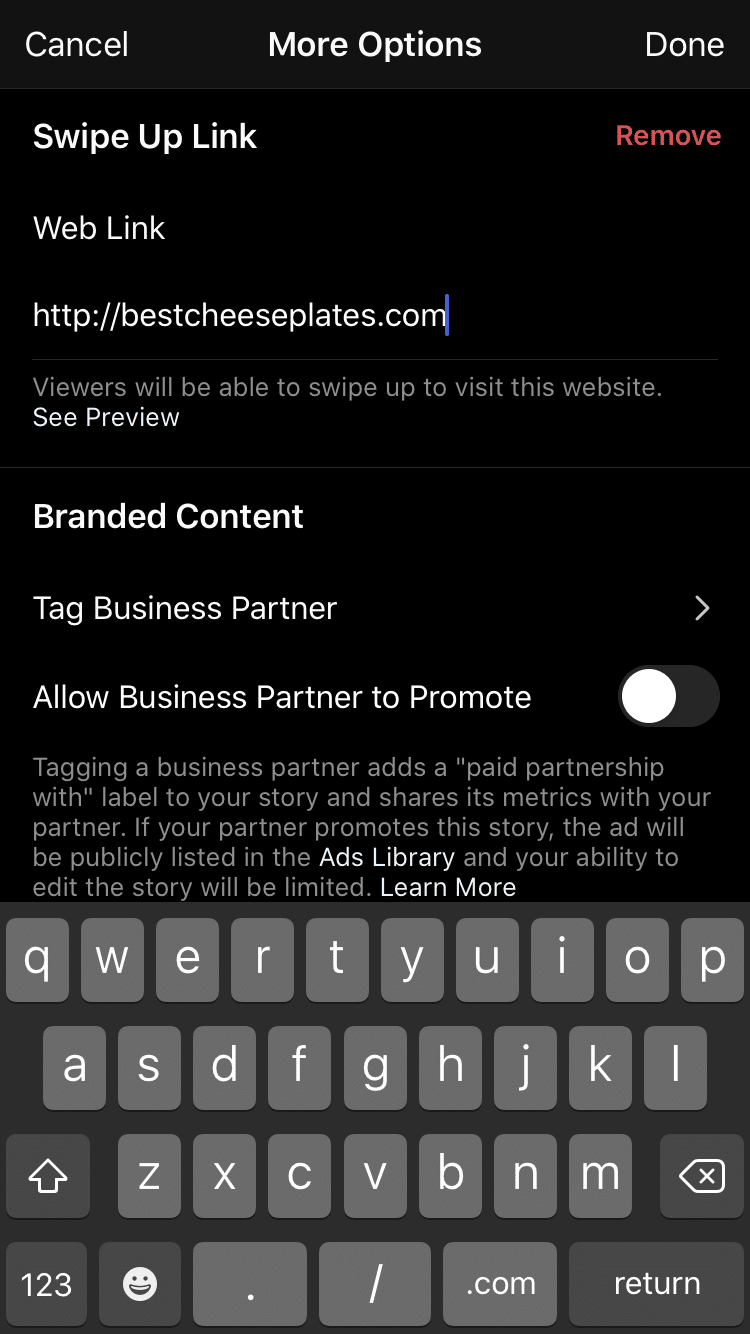
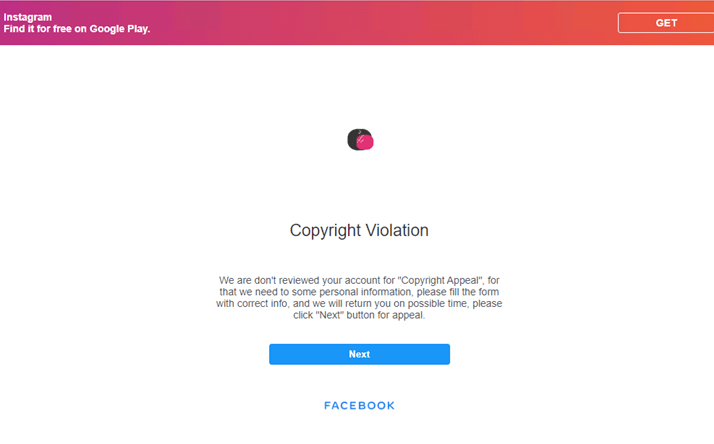
Watch Out: Instagram Hackers Are Using Fake Copyright Notices to Trick People into Giving up Their Account Details | Fstoppers



/cloudfront-us-east-2.images.arcpublishing.com/reuters/EV62MSSML5MZ5ANBN5SMOKKPDM.jpg)